X4 Server
Replace engine caches by a modern framework and remove the x4config parts
The <productionMode> entry to turn on/turn off the production mode and the <cache> entry for the definition of the engine cache were removed from the x4config.xml file. This ensures a powerful and stable caching which does not require any configuration.
Improve Profiling ReST API to facilitate the modification of the profiling configuration
The ReST Service for the Profiling Management is extended to enable the easy modification of the profiling configuration.
The profiling configuration can be updated without having to send the entire object (e.g., when deactivating, it is not necessary to send the entire process list).
Note:
The ReST API differs from the Adapter API.
The following ReST endpoints are available:
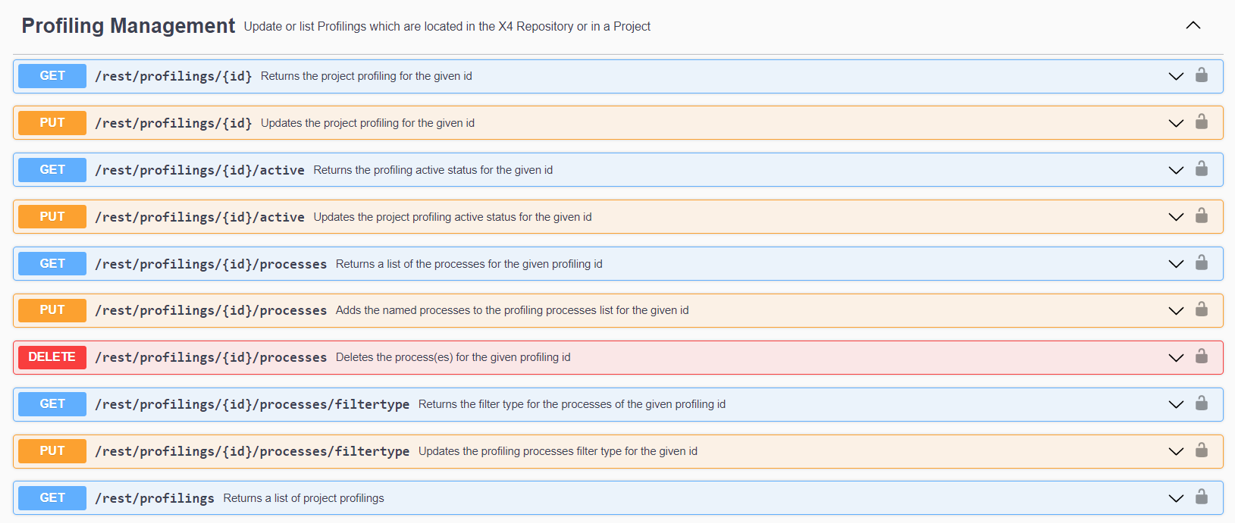
You can find more infomation on the available ReST endpoints, the input and output structure, as well as the possible values in the X4 ReST API under http://localhost:8080/X4/X4Api/.
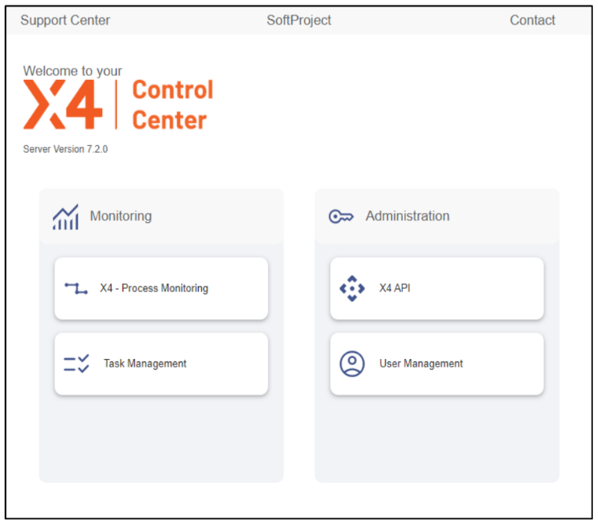
New Welcome Page at X4 BPMS Root URL
A new Welcome page has been created for the X4 BPMS root URL (e.g. localhost:8080) now called the X4 Control Center.
Scheduler – Improve Scheduler ReST API
The ReST service for the scheduler has been extended in order to allow the simple modification of the scheduler configuration.
The scheduler configuration can be updated without sending the entire object.
Note:
The ReST API differs from the adapter API.
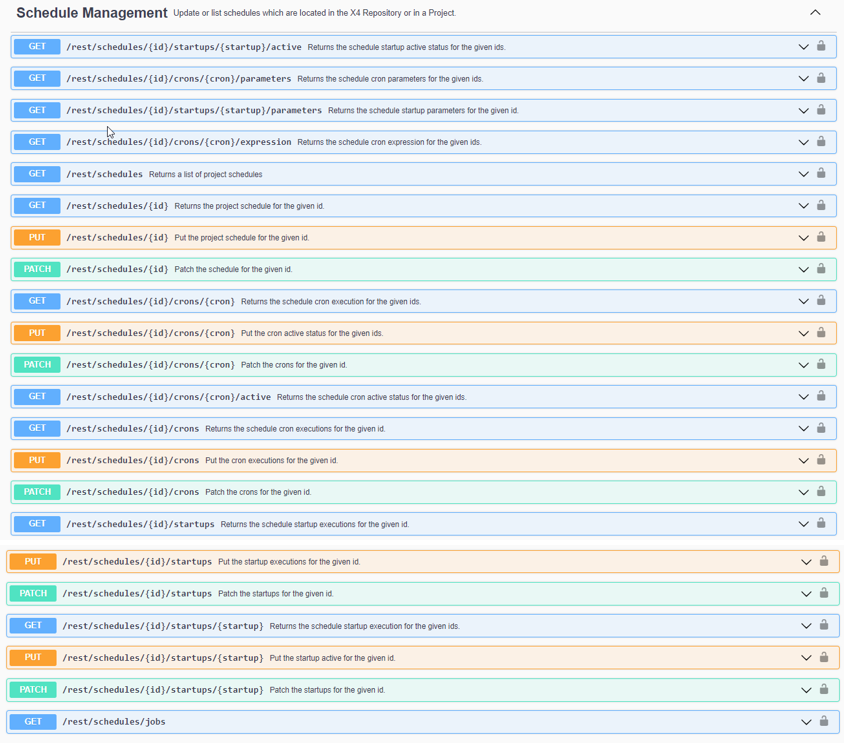
You can find more infomation on the available ReST endpoints, the input and output structure, as well as the possible values in the X4 ReST API under http://localhost:8080/X4/X4Api
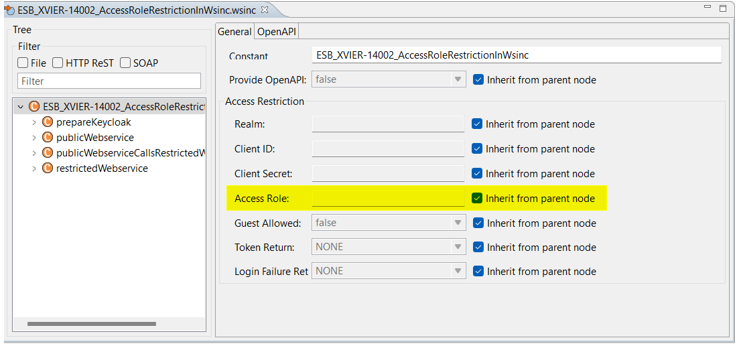
Add access role restriction to wsinc definition
To restrict access in Web Services definitions, a new Access Role field was created. It relates to a role in Keycloak and the user needs to be assigned to have access to the service.
The role is inherited from the parent node and if a user has no role access the "403 forbidden" message is issued. If the user has invalid token access, "401 unauthorized" is returned.
New parameters for process IDs
To use the new process UID in processes, a new placeholder, PUID, is available. The existing PID placeholder is still available as number.
%PID% | ID of the current Technical Process instance as integer number that is unique within an X4 Server instance. Subprocesses are executed with the same Technical Process ID. This does, however, not apply to processes that have been started using the Process Starter. If multiple instances of the X4 Server are executed simultaneously within one application server, it is recommended to use the unique placeholder %UID% instead of %PID%. |
%PUID% | Outputs the unique UUID of the start process. |
For more information, see System Parameters.
Keycloak ReST-API user replaced with a service user
The Keycloak System user is replaced by a so-called service user. The "Keycloak ReST-API User" is removed.
The server now works with so-called service accounts, using the Client ID as the account's username and the Client Secret as the account's password.
The new Keycloak configuration file will have the following structure:
{
"connection": {
"realm": "X4Realm",
"auth-server-url": "http://localhost:8085/auth/",
"resource": "X4",
"credentials": {
"secret": "60304a13-8fa6-4899-94a2-0c10562768ec"
}
},
"service-account-credentials": {
"username": "Test",
"password": "D9iRpVhaqMeTrBzBZdz2MWD7mAtapvua"
}The service-account-credentials dictionary is optional.
By default, if this key is not present in this configuration file, the server will use connection > resource as the service account ID and connection > credentials > secret as the service account secret. If the file is not deployed in the server (under the configurations directory) or if there is no connection data, the credentials will be set to X4 and 60304a13-8fa6-4899-94a2-0c10562768ec by default.
This mechanism allows the system administrator to override the default service accounts if needed, but also offering the possibility to avoid maintaining two sets of Keycloak credentials (the one in connection and the one under service-account-credentials).
If any changes are made to the Keycloak configuration file, the server must be rebooted.
Install tool for installing X4 BPMS and Keycloak as a service
X4 Server and Keycloak can be installed as a service when running the default installation. The creation of the service is done automatically, as well as the cleaning after uninstalling X4.
For more information, see the X4 BPMS Installation Guide on the Download page of the SoftProject website at softproject.de/en/downloads.
Docker compose file installing X4 BPMS and Keycloak
A docker file is available for the download of the X4 BPMS Server and Keycloak Installation Release 7.2.
For more information, see the X4 BPMS Installation Guide on the Download page of the SoftProject website at softproject.de/en/downloads.
X4 Update Tool is simpler for patch releases
The Update Tool has been enhanced to facilitate the update of minor versions. The user can create a copy of the existing version as backup. Within patches, it is not necessary anymore to migrate existing projects.
The Update tool updates the following components in the running installation:
ear
x4 WildFly modules
X4 Server supports Keycloak 19.0.0+
The X4 Server now uses Version 19.0.1 of the authentication provider Keycloak.
For more information, see the System Requirements on the Download page of the SoftProject website at softproject.de/en/downloads.
Keycloak – Create default user
The new Keycloak version does not allow to have a default Admin User. At first use, the user needs to create an Admin User manually by going to http://localhost:8085/auth/ and create a user in the Control Center via User Management.
