AES Encryption
This adapter encrypts and decrypts input data using the AES encryption algorithm.
AES Encryption
The publicly available encryption algorithm Advanced Encryption Standard (AES) is one of the most popular and secure encryption methods.
It is based on a series of byte substitutions, permutations and linear transformations that are performed on 16-byte data block – therefore the term block encryption. These operations are repeated several times, and in each of these iterations an individual iteration key calculated from the actual key is used in the calculations. If only a single bit in the key or in the data block is changed, a completely different cipher block is created – an advantage over classical encryption methods.
The designations AES-128, AES-192 and AES-256 specify the key length: 128, 192 and 256 bits. Until now, no practical attack is known for any of the AES variants. AES is therefore the preferred encryption standard.
You can find additional information on AES encryption under https://www.comparitech.com/blog/information-security/what-is-aes-encryption/.
Properties
Operation | Defines the operation executed by the adapter Possible values:
|
Parameters
Adapter | Adapter main class (do not change!) Possible values: |
password | Required for operation |
salt | Required for operation In cryptography, salt refers to a randomly selected character string that is appended to a given plaintext before further processing (e.g. input to a hash function) to increase the entropy of the input. It is often used for storing and transmitting passwords in order to increase information security. |
keyAlgorithm | Required for operation Possible values:
|
keyLength | Required for operation Possible values:
|
keyIteration | Required for operation GenerateSharedKey. Iterations to be used in order to create the shared key. |
cipherAlgorithm | Algorithm to encrypt and decrypt the input data. Possible values:
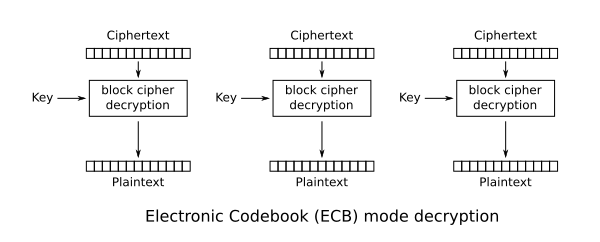
Additional information: CBC Mode and ECB Mode
|
sharedKey | Shared key to encrypt and decrypt input data (Base64 encoded). |
initializationVector | Initialization vector to encrypt and decrypt the input data; Works only in CBC mode. When encrypting messages, it is important to avoid that the same plaintext blocks always result in the same ciphertext blocks. Example: A formal letter usually begins with "Dear Mrs./Mr." followed by the name. Knowing this, an attacker could try to draw conclusions about the key used. To avoid this, the first plaintext block is linked to an initialization vector by XOR. Since the initialization vector was generated randomly, the resulting ciphertexts differ even if the plaintexts begin with identical data. |
prependInitializationVector | Determines whether the initialization vector should be used as prefix for the encrypted data. The initialization vector can be transferred to the encrypted data in plaintext without any problems, since attackers cannot obtain any information from it without the key. The initialization vector is only intended to dilute the beginning of the message before the message is encrypted. If the initialization vector is not transmitted, it must be obtained by other means, since it is necessary for decryption.
|
encoding | Required for operation Decrypt. Specifies the encoding of the decrypted data. |
mimeType | Required for operation Decrypt. Specifies the Mime type of the decrypted data. |
Status values
-1 | An error occurred during the operation's execution. For more details consult the server log. |
1 | The operation was executed successfully. |
Input
The adapter expects different input documents depending on the selected operation.
For operation
Encryptthe adapter expects any input document, e.g. XML, text or binary files.Sample input for operation Encrypt
XMLThis is a top secret message and should be AES encrypted!For operation
Decryptthe adapter expects AES-encrypted data (Base64).Sample input for operation Decrypt
XMLdpi4dqEK7yiRcyz1HdLs9yxqNLIg6u8fqGR0JxADiCdHb/6PGDqSxzID6VcuecxUP44x7bkHTggDpn8DO/bgKg==
Output
The adapter outputs different result documents depending on the selected operation.
For operation
Encryptthe adapter returns the encrypted input data (Base64 encoded).Sample output for operation Encrypt
XMLdpi4dqEK7yiRcyz1HdLs9yxqNLIg6u8fqGR0JxADiCdHb/6PGDqSxzID6VcuecxUP44x7bkHTggDpn8DO/bgKg==For operation
Decryptthe adapter decrypts the encrypted input data.Sample output for operation Decrypt
XMLThis is a top secret message and should be AES encrypted!For operation
GenerateSharedKeythe adapter returns the shared key with the key parameters defined in the adapter.Sample output for operation GenerateSharedKey
XMLSfQYr8UlXmBIeHbZE28XkquKZHFX0qfsSTGBl+4WQDM=For operation
GenerateInitializationVectorthe adapter returns a random initialization vector depending on the cipher algorithm.Sample output for operation GenerateInitializationVector
CODEJXAxGJ343MMjwLFi78z8xw==
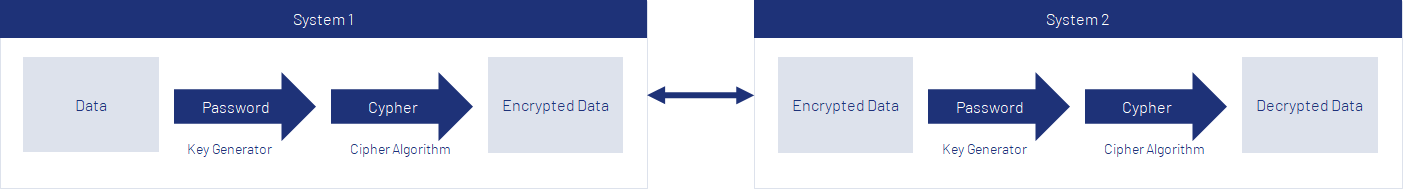
Sample Scenario:
A typical scenario is the exchange of encrypted data between two systems. One way to achieve this is to use a secret password to encrypt and decrypt the data, which is known to both systems. A key is generated from the password using the GenerateSharedKey algorithm. The key prepares the password cryptographically and ensures a stronger encryption depending on the selected algorithm. The stronger the key, the more difficult for third parties to decrypt the encrypted data.
As an alternative to the password, also the key can be provided to both systems. This approach is less secure since the additional information about the password with which the key was generated is not known.
Using the key and the cipher algorithm the data is made unrecognizable for third parties and can only be made recognizable again using the same key.
The encrypted data can now be transferred to the second system, either via a network or hardware (USB stick). Thus, no third party can use the data.
The second system also generates the key with exactly the same parameters as the first system. Together with the same cipher algorithm, the data is decrypted and can be sed.